Glewlwyd SSO server
NOTICE: This project is no longer being maintained. ⚠️
This project is now closed for me, I have no time nor motivation to maintain it, so I prefer closing this repository.
Project
Glewlwyd is mostly developped by myself on my free time, with gracious help from users.
Nevertheless, it hasn’t been fully audited or tested by external developpers.
Glewlwyd can take a central place in a system where applications and environments need authentication and authorization, be aware of the risks: bugs, non discovered vulnerabilities, etc.
I recommend not to use Glewlwyd in production, more likely to test OAuth2/OpenID behavior, MFA connections, or IdP in general. You can also explore its functionalities and help yourself with its source code for other implementations.
Experimental Single-Sign-On (SSO) server with multiple factor authentication for OAuth2 and OpenID Connect authentication
Glewlwyd 2.7.6 is available. Feel free to install it, test it, use it (with precautions!), and send feedback if you feel like it!
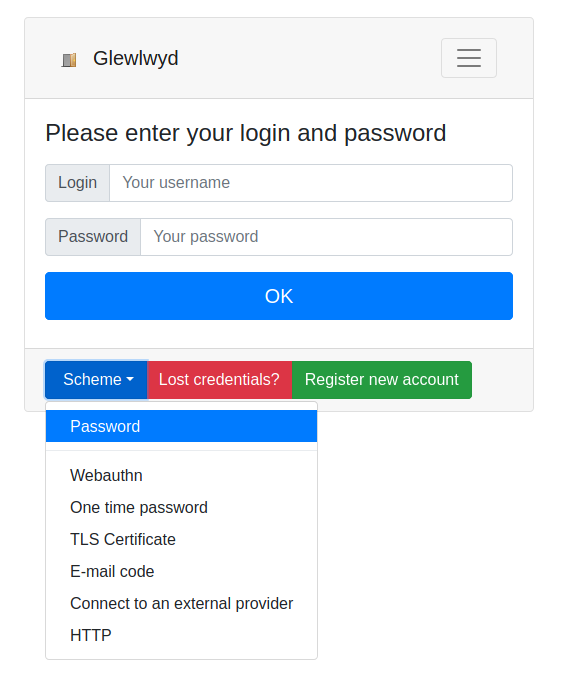
Process supported:
- OpenID Connect/OAuth2
- OAuth2: Deprecated legacy plugin, it’s recommended to use the OpenID Connect/OAuth2 process for new installations
User authentication via multiple factors:
- Password
- One-time password (TOTP/HOTP)
- WebAuthn (Yubikey, Android and Apple fingerprint or face id, etc.)
- One-time password sent via e-mail
- TLS Certificate
- External OAuth2/OIDC providers
- HTTP Backend service providing Basic Authentication
Users and clients storage backends:
User registration
New users can register a new account with the possibility to confirm their e-mail address or not. During the registration process, the new user may be expected to register their passwords, as well as other authentication factors:
- One-time password (TOTP/HOTP)
- WebAuthn (Yubikey, Android devices)
- TLS Certificate
- External OAuth2/OIDC providers
Existing users can update their e-mail by sending a confirmation link to the new e-mail.
Lost credentials
Existing users can reset their credentials if their password or authentication schemes are lost or unavailable. Credentials can be reset by different factors:
- A link sent to the user’s e-mail
- A one-time use recovery code
See the register/update e-mail/reset credentials documentation for more information on the registration, update e-mail or reset credentials features.
Based on a plugin architecture to make it easier to add or update storage backends, authentication schemes or process.
Passwordless authentication
Adding new authentication schemes or backend storage for users and clients is possible via the plugin architecture.
Architecture and performance
The backend API server is fully written in C and uses a small amount of resources.
Its plugin architecture makes it easy to add new modules or plugins, or modify existing ones with less risks to have unmaintainable code.
Installation
The full installation documentation is available in the Install documentation.
Docker
A docker image is available for tests on localhost. To test the image, run the following command:
$ docker run --rm -it -p 4593:4593 babelouest/glewlwyd:latest
And open the address http://localhost:4593/ on your browser.
- User:
admin - Password:
password
This Docker image can be used for tests or for real use by changing the configuration files. More information in the install documentation.
Getting started
The Getting started documentation will help administrators configure Glewlwyd’s modules and authentication schemes.
User documentation
The user documentation will help Glewlwyd’s users manage their profile and log in to Glewlwyd.
Core API
The full core REST API documentation is available in the API documentation
Plugins architecture
You can update the existing plugins or add new ones depending on your needs, check out the documentation available for each type of plugin:
- User backend modules
- User middleware backend modules
- Client backend modules
- Authentication schemes modules
- Plugins (Register, OAuth2 or OIDC plugins)
Screenshots
Go to the Screenshots folder to get a visual idea of Glewlwyd.
Questions, problems or feature requests
You can open an issue, a pull request or send me an e-mail. Any help is much appreciated!